In our technology-driven world, efficient IT support is the backbone of any successful business. From ensuring seamless operations to safeguarding sensitive data, reliable IT services are crucial for maintaining productivity and protecting your bottom line.
Blog
Tech tips, news, and expert insights
How Phoenix SMBs Can Easily Eliminate Tech Problems In Their Office

Now more than ever, we rely on technology to run our businesses and our lives. When the “Internet goes down,” most businesses come to a standstill until they are back online, costing thousands in lost productivity and sales. A perfect example would be the AT&T outage that happened a few weeks ago, when an estimated 1.7 million customers, including small business owners, lost service.
Suspect Your Computer Has Been Hacked? Do These 5 Things Now!

The initial reaction when you suspect your computer or network has been compromised is to panic. However, if your network has been breached, what you do next can make the difference between the incident being a minor inconvenience and being a devastating disaster that brings legal trouble and huge fines, and halts your ability to do business.
Financial Advisor Loses $50K To A Scammer

Horror stories of people getting scammed out of hundreds or even thousands of dollars aren’t in short supply. As we scroll through the news app from the comfort of our couch, reading these accounts of how a stupid so-and-so opened an obviously suspicious attachment and a hacker drained their bank account, it’s easy to say things like “I’d never fall for that!” But would you?
The sobering truth is that, under the right conditions and with the right threat, anyone can fall victim to a financially devastating scam.
AI Got Your Tongue?
Is Your Digital Life Encrypted?

Introduction
Imagine you have a secret message you want to send to your friend, but don’t want anyone else to read it. If they have the “key” to reading it, then only the intended recipient can decipher what you mean.
Encryption is like that secret code you and your friend create to lock the message, making it look like gibberish to anyone else who finds it.
Is TikTok Really Getting Banned in the U.S.?
What Is ‘5G’?

Introduction
Do your devices run on 5G?
Do you know what 5G even is?
5G indicates the fifth generation of mobile networks. In other words, it’s the wireless technology that your smartphone uses to run and is touted as 200 times faster than the previous generation, 4G. Turn off your phone’s WiFi to find out what generation you’re running on.
RaaS: What Are These Kits
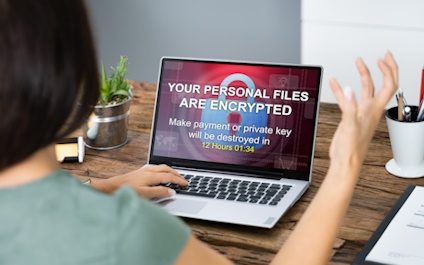
Imagine a threat actor determined to target YOUR data and finances. It would take a LOT of time, effort and money to build ransomware code all on their own, let alone to build a whole email campaign convincing you to fall for their tricks…Now imagine they could simply buy ransomware off the Dark Web, completely ready-made to launch against you?
Unfortunately, that’s a very real scenario.





